Beyond Antivirus: Modern Endpoint Security

15 Dec 2025
Beyond Antivirus: Modern Endpoint Security
In today's digital age, cyber threats are no longer minor annoyances, but real risks that can disrupt business operations, steal important data, and damage a company's reputation. Technological developments, cloud adoption, and hybrid work patterns make devices such as laptops, servers, and mobile devices prime targets for cyber-attacks. Therefore, endpoint protection is one of the key foundations of a modern company's IT security strategy.
The Increasingly Complex Development of Cyber Threats
Initially, cyber threats generally took the form of simple malware that could be detected with database- or signature-based antivirus software. However, over time, attack methods have become much more sophisticated. Cybercriminals now use techniques designed to evade detection, exploit unknown security vulnerabilities, and spread rapidly within networks.
Modern threats no longer rely solely on malicious files, but also exploit user behavior, system vulnerabilities, and file-less attacks. This situation renders traditional security approaches inadequate.
The Evolution of Endpoint Protection
To address these challenges, endpoint security solutions have also evolved:
-
Traditional antivirus (AV) focuses on detecting known threats through signature databases. This approach was effective in its time, but has limitations when dealing with new threats.
-
Next-generation antivirus software (NGAV) uses behavioral analysis to detect suspicious activity, enabling it to recognize previously unregistered threats.
-
The Endpoint Protection Platform adds a broader layer of prevention, such as device control, attack surface reduction, and proactive security policies at the endpoint.
-
Endpoint Detection and Response (EDR) combine all of these approaches with centralized monitoring, investigation, and incident response capabilities, giving IT teams deeper visibility into every security event.
This evolution shows that endpoint protection is no longer just about prevention but must also be able to detect and respond to threats quickly and accurately.
Endpoint Security Challenges in Companies
Many organizations still face challenges in endpoint security, such as limited IT resources, the complexity of managing multiple security tools, and delays in responding to incidents. Non-integrated solutions often generate numerous alerts without clear context, making it difficult for IT teams to take effective action.
This is where a smarter, integrated, and easy-to-manage endpoint solution is needed.
SentinelOne as a Modern Endpoint Security Solution
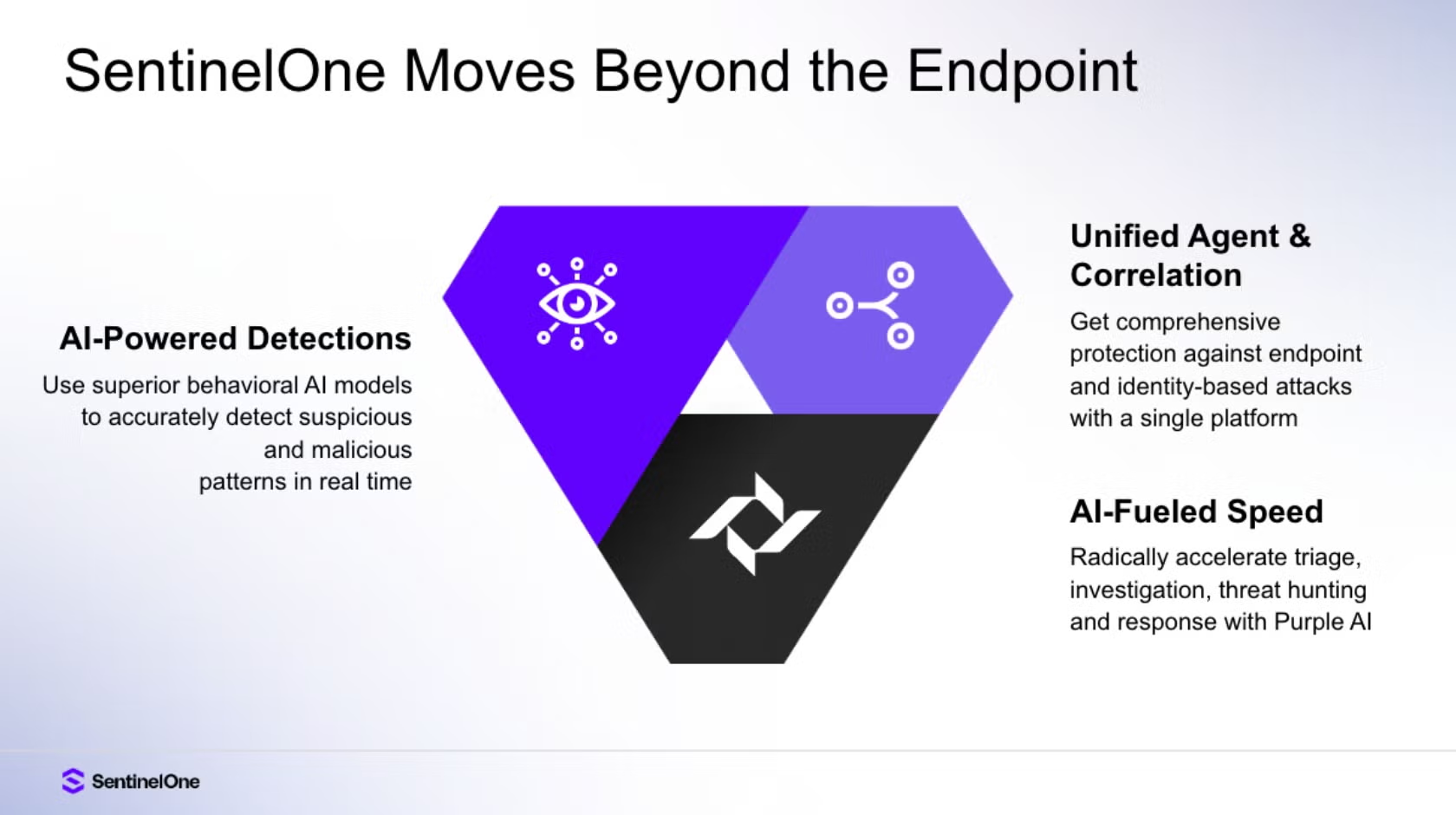
SentinelOne is a modern endpoint protection solution designed to combat today's cyber threats. This solution protects various types of endpoints, from user devices to servers and cloud environments, in a single integrated platform.
SentinelOne works with a behavior-based approach, rather than relying solely on a threat database. This allows the system to detect malicious activity in real time, including previously unknown attacks.
In addition to detection, SentinelOne is also capable of automatic response, such as stopping malicious processes, isolating infected endpoints, and restoring systems to a secure state without disrupting business operations. This helps companies minimize the impact of attacks and speed up the recovery process.
The SentinelOne platform also provides clear visibility for IT teams through a centralized dashboard, so that every security incident can be understood in its full context and followed up on more quickly.
Perkom's Role in SentinelOne Implementation
As an IT solutions and services provider, Perkom not only delivers SentinelOne technology, but also ensures its implementation runs optimally according to customer business needs.
Perkom assists companies through the process of endpoint security needs analysis, solution planning and implementation, to ongoing assistance and support. With this approach, companies can ensure that their endpoint security investments provide truly effective and sustainable protection.
Author: Ghea Devita
Marketing Communication, PT Perkom Indah Murni